
Since we started EZKL, some users have repeatedly asked the following:
Alice owns a private model, Bob owns private data. How do they compute an EZKL proof of Alice’s model applied to Bob’s data while keeping both model and data confidential to their respective owners?
Keeping both the model and the data private to their respective parties would be a significant breakthrough. With typical ZK-SNARKs, this is impossible: the prover must possess the entire witness to compute the proof. So Alice, Bob, or a third party would need full access to both the model and the data.
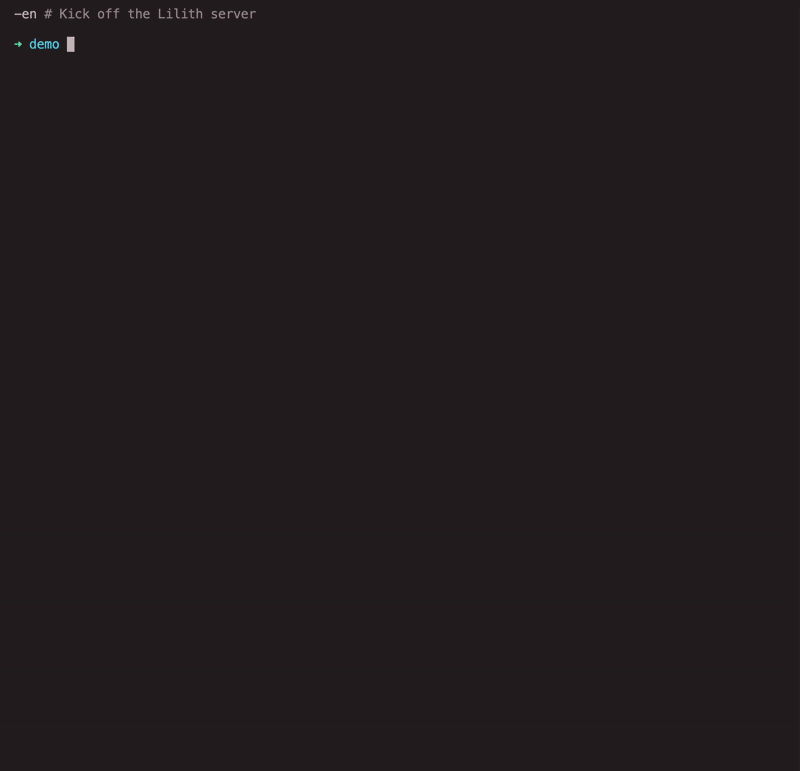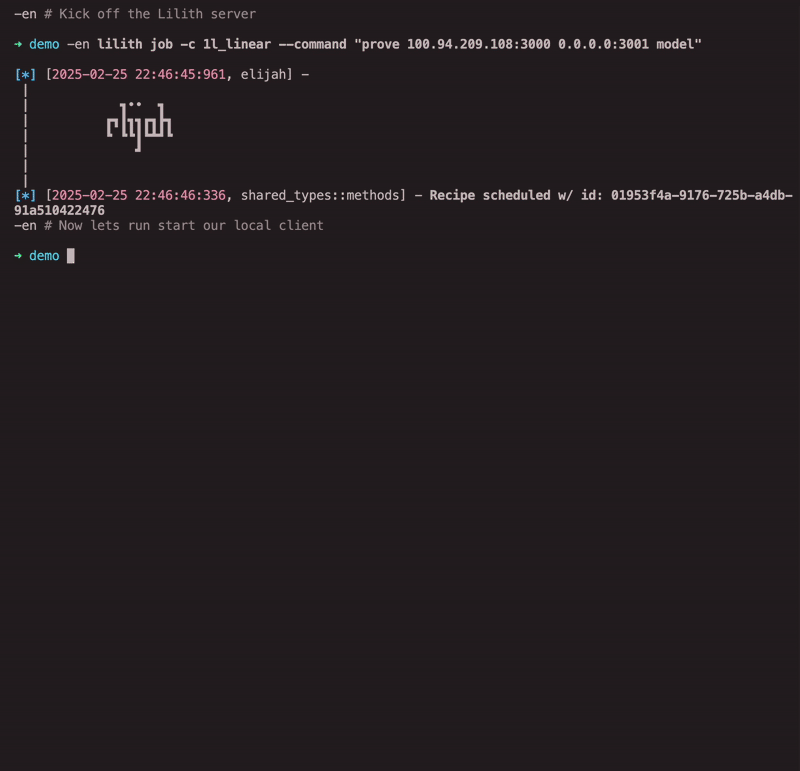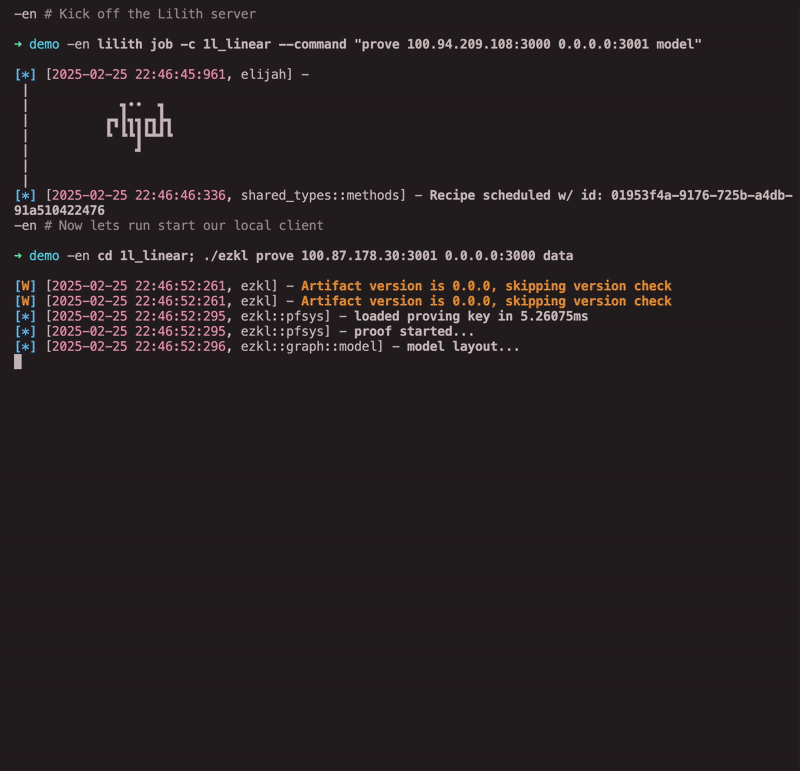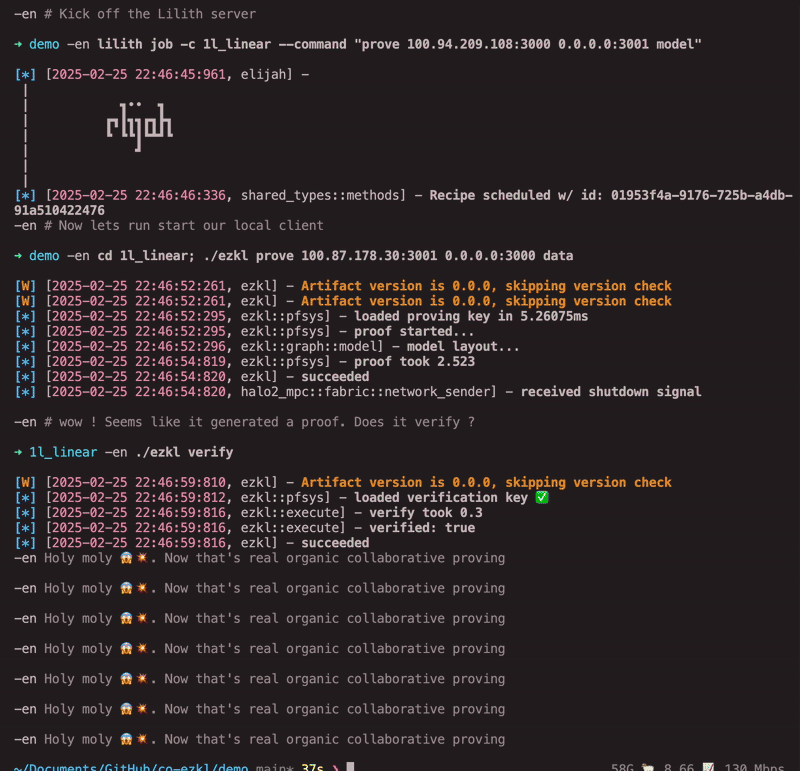
We are thrilled to announce that this workflow is now possible!
Introducing Collaborative SNARKs for EZKL
Our brand-new collaborative SNARKs (cosnarks) implementation, led by Halo2 co-author Ying Tong Lai, overcomes this longstanding constraint. This enables truly collaborative zero-knowledge proofs while maintaining confidentiality for all parties using the EZKL framework.
Using Cosnarks with EZKL
We’ve made using cosnarks with EZKL dead simple. You can reuse existing proving and verification keys and only need to change your proving step.
A local proof looks like this:
ezkl prove
Now you can collaboratively compute a proof like this:
ezkl prove --remote-peer <REMOTE_PEER> --local-addr <LOCAL_ADDRESS> --id "data" or "model"
You specify the remote peer you want to collaborate with, the local address you want to listen on, and whether you are providing the model or data parts of the proof! That’s it.
Even BETTER, we’ve already integrated cosnark proving on Lilith. You can quickly spin up cosnark peer servers with a single command 😱:
lilith job -a <PROJECT_NAME> --command "prove --remote-peer <YOUR_LOCAL_ADDR> --local-addr <THE_PORT_TO_SERVE_ON_LILITH> --id model"
Your local peer that isn’t on Lilith just needs to be dialable via a public IP address 🤗
What Can You Do With This?
Decentralized Finance (DeFi)
- Confidential Tradings & Dark Pools with Complex Logic: Submit orders to dark pools running sophisticated strategies without exposing your order flow to prying eyes.
- Private Lending & Credit Scoring: Get approved based on your financials without actually sharing them! Lenders can assess creditworthiness without seeing sensitive data or leaking their underwriting model.
Identity and Fraud Protection
- Prove you’re legitimate without learning how the fraud system works (so you can’t game it) and without exposing your personal data!
- Verify your identity with face matching where Alice’s model never sees Bob’s face, and Bob never learns the model.
Confidential Collaboration
- Run joint statistical analysis across companies without revealing proprietary datasets to each other. Prove you included all data points without showing what they are!
- Double-blind model-driven matching where both sides find ideal counterparties without exposing preferences or strategies.
Other Cool Stuff with Shared Private State
- Asynchronous microrollups using big fully private shared state and arbitrary PyTorch/Tensorflow/Pandas updates!
How It Works
Cosnarks use secret sharing and multi-party computation (MPC) to allow two or more parties to engage in arbitrary compute over partially private, partially shared data. The magic? They can produce a zero-knowledge proof without revealing the confidential parts to each other!
At a high level, it happens as follows. The data owner splits each value into two shares, both of which are required to reconstruct the data point, and shares one with the model owner. The model owner learns nothing about the data from this share, and does the same with the values constituting the model. Then the parties step through the usual proof creation process, but most of it takes place on these “encrypted” values or combinations thereof (e.g. a share of a data value plus a share of a model value). Addition happens locally, but multiplication requires communication. Some tricks can be applied to minimize the bandwidth required.
You might worry that adding MPC to proof computation would explode resource usage, but Alex Ozdemir and Dan Boneh showed that you can get it almost for free: you pay the cost of MPC plus the cost of ZK, but that’s essentially it. So this past summer, after a conversation with Alex and Dan, we began working with Ying Tong on implementing collaborative snarks for EZKL. After seven months of work, the beta is ready!
Two-Party, Not Delegated Proving
MPC schemes can vulnerable to collusion — if there are 3 or 10 node operators, even if you supposedly know who they are, there is no way to really know they have not colluded to learn your private data (or that they are not really all the same party). Thus there is a trust assumption in delegating proving (or anything else) to a set of MPC operators. We are not doing delegated proving here: both parties cooperating to make the proof have something confidential to protect. Think of it this way: there is no possibility of collusion and no additional trust assumption needed because you are one of the parties. That is one of the reasons we have chosen to focus on the two-party (2PC) case. 2PC also allows for some optimizations not available in the general many-party case; our work leans heavily on Renegade’s 2PC-optimized MPC library. And of course, we think the 2PC use cases that our users have asked for are particularly compelling.
Acknowledgments
- This work uses Renegade’s ark-MPC library as scaffolding, which is optimized for two parties.
- Many thanks for Alex Ozdemir and Dan Boneh for their help in kicking off this work.
- And of course, Ying Tong, who has been the driving force behind this project.
Future work
Currently proving effort is shared equally amongst the two parties and both need to supply equal amounts of compute (and memory usage) to complete the collaborative proof. Given that much private data resides on mobile phones, and that the source of this data can be attested to (particularly in the Apple ecosystem, for eg. your phone camera etc…). Introducing asymmetry to the collaborative proof, whereby the data provider expends less compute than the model provider (which we can expect to be hosting a server anyway) is of great interest and would complement our recent iOS bindings, and metal acceleration; and complement some of our users that are mobile first like Sundial’s identity and KYC solution (see here).
Asymmetric MPC is an active area of research and we’ll be exploring this in the coming months.
<3
Collaborative SNARKs in EZKL open powerful new possibilities across finance, identity, and data collaboration. Private trading strategies can now interact with confidential market data. Identity verification can happen without exposing personal information or proprietary models. Organizations can collaborate on sensitive datasets while maintaining complete confidentiality.
Our implementation makes this sophisticated cryptography accessible through simple commands and seamless Lilith integration. Building on established research and optimized for the two-party case, we’ve created a practical solution that requires minimal changes to existing workflows (basically NONE 🤗).
We’re so hyped to see what you guys will build with this. We’re currently running trials with co-EZKL in closed beta before a broader public release. If you’re interested in joining, please reach out to us.
As always, come join our Discord, we’ll welcome all your ideas with open arms.